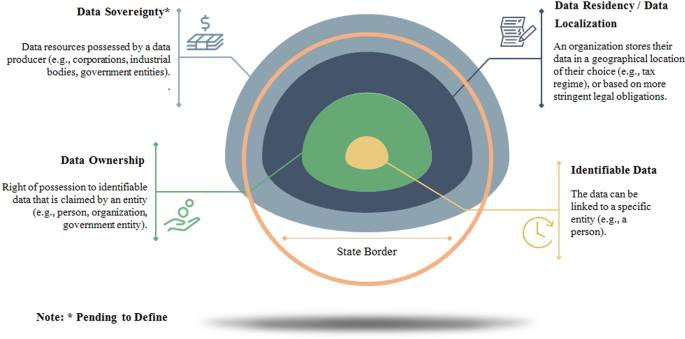
Finding a dedicated terminology could help resolve long-standing debates about various data disputes (Figure 1), such as where and how to demarcate data resources in cyberspace (Kalir and Maxwell, 2002). The purpose of the coining of the term “data sovereignty” is to remove the misconception that data resources rightfully belong to the data creators, rather than the people or states providing the data. Regulations in certain countries allocate ownership of data to nations, potentially significantly disrupting the path to a thriving global “data” economy. For example (Bogaerts and Segers, 2018).
Russia's Personal Data Law (OPD-Law) requires that data relating to citizens be stored, updated, and retrieved only in data center resources located within the Russian Federation. While such laws tend to enhance the privacy of citizens from other countries, they also tend to be motivated by national protectionism and help businesses and governments realize the full potential of cross-border, global data. tend to contribute to the creation of border-based data silos that prevent flow. When negotiating trade agreements, the United States hopes that the European Union “will not impose measures (such as tariffs) that restrict the flow of data across borders” and “will not require the use of data” (Office of the U.S. Trade Representative). , 2019). or the establishment of local computing facilities. ” The United States has taken a different attitude towards China and is seeking to prevent the leakage of private and private information by closing a US$1.2 billion deal between TikTok and MoneyGram and Ant Financial (a conglomerate owned by Alibaba Express). (StraitsTimes.Com, 2018) at the hands of foreign entities that they believe are freely sharing information with foreign governments. Our definition runs counter to digital sectarianism and the “splinternet” (Box, 2019) and may therefore generate controversy in both academia and industry. We recommend harnessing the power of decentralized markets to protect your data through non-legislative actions, namely generation and protection from attacks.
When it comes to data, “access to data takes precedence over ownership (Ogilvy, 2017),” so data sharing and portability rights are often the main products sold or traded to external organizations. Similar to the transfer of national sovereignty in international relations (Taylor, 1997), the concept of data sovereignty enables the transfer of rights for the purpose of data sharing and portability. Data sovereigns can transfer partial rights to governments or competitors in other industries through moderate negotiations. Such transfers are proactive and strategic when they are developed by anticipating or analyzing trends and considering the organization's past performance with respect to externally induced crises and threats. For data resources, these defensive transfers often cause or result in significant loss of data asset valuation, making it too late to perform reactive transfers when the opportunity arises. is common.
The Internet Archive was founded by Brewster Kahle to preserve vast amounts of the World Wide Web. Recent attacks on the Internet Archive were carried out by the National Writers Union of the United States and several digital publishing companies (Hasbrouck, 2020). They listed his five distribution channels that show how authors (and publishers) are harmed by the existence of archives. This includes (1) downloads via his OpenLibrary.org of e-books assembled from page images, and (2) audiobooks generated from scanned images. API for pages, (3) displaying OpenLibrary.org page images, (4) displaying Archive.org page images, and (5) automatically downloading page images. In response to their attack on the Internet Archive, Karl pointed out that “many of these books are no longer available for sale in their original book form.” Because royalties are not collected on books that are no longer available for purchase in their original format, publishers and authors lack a valid economic argument for the harm caused by the Internet Archive collating this material.
Data sovereigns, who are inherently concerned with the movement of data, may follow the free flow of data across geopolitical boundaries. We take for granted that we live in an interconnected world. The adoption of “data sovereigns” will properly define the boundaries of cyberspace. For example, the European “right to be forgotten,” which gives European Union citizens the power to request the erasure or restriction of data about them, is subject to European Union regulation (unless a trade agreement specifies otherwise). Applies only within the borders of the European Union. ) (Court of Justice of the European Union, 2019).
The concept of data sovereignty enables economic agglomeration in cyberspace. Using data as an economic resource usually involves the threat of new entrants and substitute products. If a data sovereign is unable to effectively protect his data and his resources, it may be wise to join a data sovereign alliance to increase protection. This concept of “data sovereignty” could help form data industry clusters in cyberspace and grow the global data economy through collaboration. Collective active defense and transfer reflects the subjective willingness of data sovereigns to harness decentralized market forces to protect their data through non-legislative action. For example, co-locating multiple organizations' computer servers in a secure data center can improve security and provide economic benefits in terms of rent, staffing, and more efficient use of large air conditioning systems to reduce power consumption. Masu. that such aggregation is no longer aimed at optimizing the internal flow of data, but seeks to form a strategic defense in the form of physical and virtual fortresses built by the data sovereignty complex; Please note.